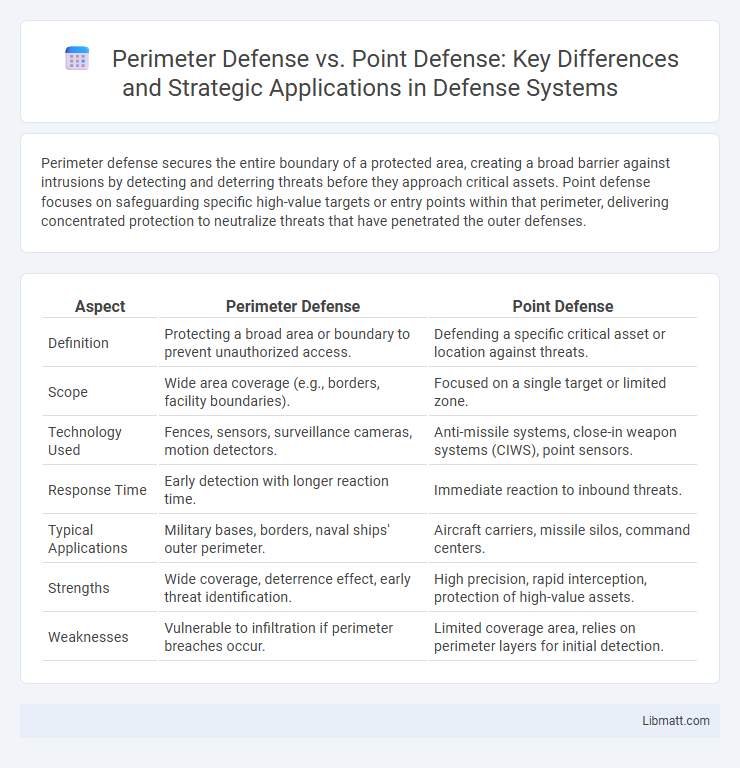
Perimeter defense secures the entire boundary of a protected area, creating a broad barrier against intrusions by detecting and deterring threats before they approach critical assets. Point defense focuses on safeguarding specific high-value targets or entry points within that perimeter, delivering concentrated protection to neutralize threats that have penetrated the outer defenses.
Table of Comparison
| Aspect | Perimeter Defense | Point Defense |
|---|---|---|
| Definition | Protecting a broad area or boundary to prevent unauthorized access. | Defending a specific critical asset or location against threats. |
| Scope | Wide area coverage (e.g., borders, facility boundaries). | Focused on a single target or limited zone. |
| Technology Used | Fences, sensors, surveillance cameras, motion detectors. | Anti-missile systems, close-in weapon systems (CIWS), point sensors. |
| Response Time | Early detection with longer reaction time. | Immediate reaction to inbound threats. |
| Typical Applications | Military bases, borders, naval ships' outer perimeter. | Aircraft carriers, missile silos, command centers. |
| Strengths | Wide coverage, deterrence effect, early threat identification. | High precision, rapid interception, protection of high-value assets. |
| Weaknesses | Vulnerable to infiltration if perimeter breaches occur. | Limited coverage area, relies on perimeter layers for initial detection. |
Introduction to Defense Strategies
Perimeter defense establishes a wide protective boundary using barriers, sensors, and patrols to detect and deter threats before they reach critical assets, ensuring comprehensive area security. Point defense concentrates resources on safeguarding specific high-value targets with rapid-response systems like automated turrets, close-in weapon systems, or specialized personnel, maximizing protection at critical points. Both strategies integrate advanced technologies and threat intelligence to enhance situational awareness and response effectiveness in diverse security environments.
Defining Perimeter Defense
Perimeter defense refers to a security strategy that establishes multiple layers of protection along the outer boundary of a property or network to detect and deter intrusions before they penetrate the core area. This method emphasizes early threat identification by monitoring gates, fences, surveillance cameras, and access control points, reducing the risk of unauthorized entry. Your perimeter defense serves as the first line of security, creating a buffer zone that prevents attackers from reaching critical assets inside.
Understanding Point Defense
Point defense targets specific assets or areas with concentrated firepower to intercept incoming threats such as missiles or aircraft before they reach critical points. This highly focused approach enhances the protection of key installations or vehicles by using radar-guided interceptors and close-in weapon systems. Understanding point defense helps you evaluate its effectiveness compared to broader perimeter defense strategies for safeguarding vital resources.
Key Differences between Perimeter and Point Defense
Perimeter defense establishes a broad security boundary around an area, using sensors and barriers to detect and deter intrusions before they reach critical assets. Point defense concentrates protection on specific high-value targets, deploying localized measures like close-in weapon systems or targeted alarms for immediate threat neutralization. Your security strategy's effectiveness depends on choosing between comprehensive early warning and focused rapid response based on the threat landscape.
Advantages of Perimeter Defense
Perimeter defense offers comprehensive protection by creating a secure boundary that deters unauthorized access before threats reach critical assets. This approach allows for early detection and response, reducing the risk of breaches and minimizing potential damage. Implementing perimeter defense enhances overall security posture by integrating multiple layers of surveillance, physical barriers, and threat detection systems to address diverse attack vectors effectively.
Benefits of Point Defense
Point defense systems offer targeted protection by intercepting threats at specific high-value assets, minimizing collateral damage and optimizing resource allocation. These systems deliver rapid response times and high precision, enhancing the security of critical infrastructure and military units. Your defense strategy gains effectiveness through concentrated force, reducing the risk of breach in vital areas.
Limitations of Perimeter Defense
Perimeter defense often struggles with blind spots and delayed response times, making it less effective against sophisticated intrusions or insider threats. Its reliance on physical barriers and sensor range can be circumvented by attackers using stealth tactics or advanced technologies. This approach also tends to create a false sense of security, potentially leading to insufficient internal monitoring and response capabilities.
Drawbacks of Point Defense
Point defense systems exhibit limitations such as restricted coverage areas, leaving vulnerabilities against coordinated or multiple simultaneous attacks. Their effectiveness often depends on rapid detection and response times, which can be hindered by system malfunctions or electronic countermeasures. Moreover, high maintenance costs and the need for continuous human or automated monitoring reduce operational efficiency compared to broader perimeter defense strategies.
Real-World Applications and Examples
Perimeter defense systems, such as security fences and surveillance cameras, are widely used in military bases and border security to detect and deter unauthorized access over a broad area. Point defense systems, exemplified by missile interceptors like the Iron Dome or close-in weapon systems (CIWS) on naval ships, protect critical assets by targeting and neutralizing incoming threats in real-time at specific locations. These approaches complement each other in comprehensive security strategies, combining wide-area monitoring with rapid-response interception.
Choosing the Right Defense Strategy
Selecting the appropriate defense strategy depends on the specific threats and asset layout, with perimeter defense focusing on creating a secure boundary around an entire area and point defense concentrating on protecting critical assets within that boundary. Perimeter defense employs barriers, sensors, and patrols to detect and deter intruders before they reach key infrastructure, ideal for large, open areas requiring early warning systems. Point defense uses localized protection measures such as cameras, motion detectors, and security personnel to respond quickly to breaches, making it suitable for high-value targets requiring concentrated security efforts.
perimeter defense vs point defense Infographic
 libmatt.com
libmatt.com