A secure enclave offers hardware-based isolated execution environments to protect sensitive data and code within a device, ensuring confidentiality even if the main system is compromised. An air gap physically isolates a system from unsecured networks, providing maximum security by preventing any remote unauthorized access or data exfiltration.
Table of Comparison
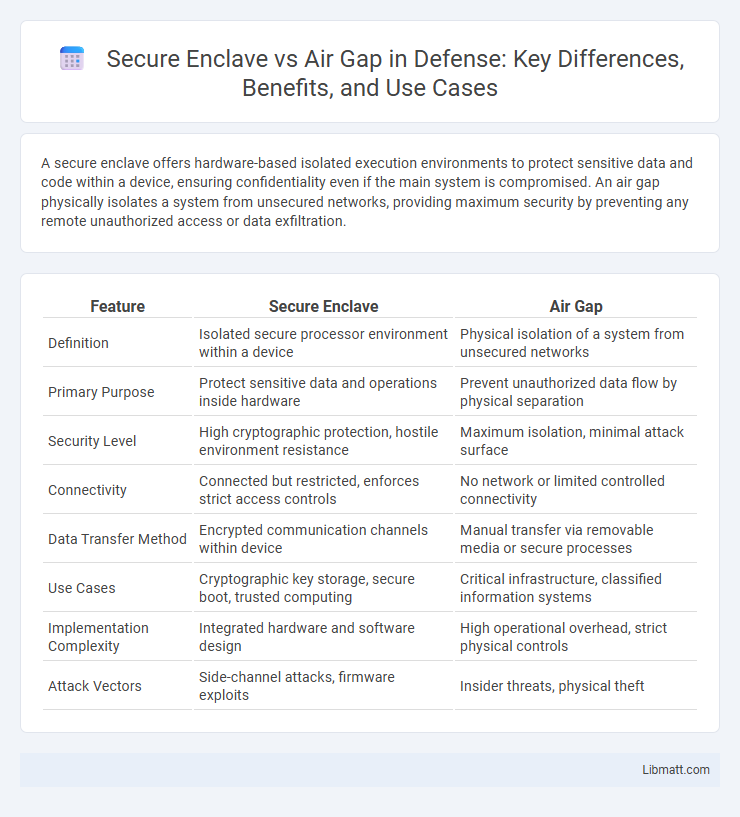
| Feature | Secure Enclave | Air Gap |
|---|---|---|
| Definition | Isolated secure processor environment within a device | Physical isolation of a system from unsecured networks |
| Primary Purpose | Protect sensitive data and operations inside hardware | Prevent unauthorized data flow by physical separation |
| Security Level | High cryptographic protection, hostile environment resistance | Maximum isolation, minimal attack surface |
| Connectivity | Connected but restricted, enforces strict access controls | No network or limited controlled connectivity |
| Data Transfer Method | Encrypted communication channels within device | Manual transfer via removable media or secure processes |
| Use Cases | Cryptographic key storage, secure boot, trusted computing | Critical infrastructure, classified information systems |
| Implementation Complexity | Integrated hardware and software design | High operational overhead, strict physical controls |
| Attack Vectors | Side-channel attacks, firmware exploits | Insider threats, physical theft |
Understanding Secure Enclave Technology
Secure Enclave technology leverages a dedicated coprocessor to create an isolated environment that protects sensitive data and cryptographic operations from unauthorized access, even if the main system is compromised. Unlike an air gap, which physically separates a device from any network to prevent data leaks or cyberattacks, Secure Enclave offers continuous, hardware-based encryption and authentication without sacrificing connectivity. Your data benefits from real-time protection through Secure Enclave's integration into devices, ensuring secure key management and encrypted execution of critical processes.
What is an Air Gap System?
An Air Gap System is a security measure that completely isolates a computer or network from unsecured networks, including the internet, by physically disconnecting it to prevent unauthorized access or data leakage. Unlike Secure Enclaves, which create protected zones within the same device for sensitive data processing, Air Gap Systems rely on physical separation to safeguard critical information and systems. Your data benefits from the highest level of protection by eliminating direct network communication, making Air Gap Systems ideal for protecting highly confidential or sensitive environments.
Core Differences: Secure Enclave vs Air Gap
A Secure Enclave is a hardware-based security feature that encrypts and isolates sensitive data within a device, ensuring it remains protected even if the main system is compromised. An Air Gap, by contrast, physically isolates a system or network from unsecured networks, preventing any external digital communication and eliminating remote access risks. Your choice between these methods depends on whether you prioritize data encryption within a connected environment (Secure Enclave) or complete physical separation to mitigate cyber threats (Air Gap).
Threat Models: Comparing Attack Surfaces
Secure enclave technology minimizes attack surfaces by isolating sensitive computations within a hardware-based trusted execution environment, protecting against software-level threats and insider attacks. Air gap security eliminates network-based attack vectors by physically isolating systems, effectively preventing remote exploits but remaining vulnerable to insider threats and physical access breaches. Comparing threat models, secure enclaves address sophisticated malware and side-channel attacks, while air gaps primarily mitigate risks from external network intrusions and malware propagation.
Performance and Usability Considerations
Secure enclave technology enhances performance by enabling encrypted data processing within isolated hardware environments, minimizing latency and maintaining system responsiveness. Air gap security, while providing robust isolation by physically separating networks, often results in reduced usability due to limited real-time data access and slower data transfer methods. Balancing performance and usability depends on the specific security requirements and operational workflows, with secure enclaves offering a more seamless user experience in connected environments.
Real-world Use Cases for Secure Enclaves
Secure enclaves provide a trusted execution environment widely adopted in industries like finance for secure transaction processing and in healthcare to protect sensitive patient data during computation. Unlike air gaps, which physically isolate systems to prevent breaches, secure enclaves enable confidential data processing within connected devices while maintaining high security standards. Real-world examples include Apple's Secure Enclave managing cryptographic keys on iPhones and Intel SGX protecting proprietary algorithms in cloud computing environments.
Practical Applications of Air Gapping
Air gapping is commonly used in high-security environments such as military networks, critical infrastructure systems, and financial institutions to prevent cyberattacks by physically isolating sensitive devices from unsecured networks. Your data remains protected by ensuring no direct or wireless connections exist between air-gapped systems and external networks. This method is particularly effective for safeguarding classified information, offline backups, and industrial control systems from remote hacking attempts.
Compliance and Regulatory Implications
Secure enclaves provide hardware-based isolation that meets stringent compliance standards such as HIPAA, GDPR, and PCI DSS by ensuring sensitive data remains protected within encrypted memory regions. Air gap techniques physically isolate critical systems from unsecured networks, making them highly effective for meeting regulatory requirements in high-security environments, including defense and financial sectors. Both methods support regulatory compliance by minimizing unauthorized data access, with secure enclaves offering continuous encrypted processing and air gaps preventing external network breaches.
Cost and Implementation Challenges
Secure enclave technology offers robust data protection within a system's processor but requires significant investment in specialized hardware and integration expertise, leading to higher initial costs and complexity. Air gap security mandates physical isolation of systems from unsecured networks, which reduces cyberattack surfaces but incurs expenses related to dedicated infrastructure, maintenance, and operational inefficiencies. Both methods face implementation challenges: secure enclaves demand compatibility with existing software environments, while air gapping complicates data transfer workflows and scalability in modern enterprise settings.
Choosing the Right Solution for Your Security Needs
Secure enclaves provide hardware-based isolated environments that protect sensitive data and computation within a device, ideal for scenarios requiring secure processing without external network exposure. Air gaps physically isolate systems from unsecured networks, offering maximum protection against remote cyber threats, well-suited for critical infrastructures and highly confidential operations. Selecting between secure enclaves and air gaps depends on the balance between operational efficiency, required security level, and the specific risk profile of your environment.
Secure enclave vs Air gap Infographic
 libmatt.com
libmatt.com